

HIPAA Won’t Save You: Why Compliance Fails Against Modern Cyber Threats
Through my work at Cyber News Live, I have analyzed numerous healthcare data breach reports, uncovering critical patterns that expose fundamental weaknesses in the industry’s cybersecurity. The sheer volume is a blaring siren, but the truly chilling pattern is this: a shocking number of these devastated organizations claimed to be “HIPAA compliant.”
They had the policies in a binder. They had the signed agreements. But when a real-world cyberattack hit, those compliance documents were as effective as a paper shield. Their digital doors were kicked wide open, exposing the most sensitive data of millions of patients and leaving the organizations facing financial ruin and a permanent loss of trust. This experience taught me a truth that every healthcare leader from the CISO of a large hospital to the owner of a small private practice must understand: compliance does not equal protection.
If you run a small clinic, you are not “too small to be a target.” To a hacker, your patient data is a valuable asset, and a smaller security budget often makes you an easier target. The Health Insurance Portability and Accountability Act (HIPAA) is the bare-minimum floor for privacy. Relying on it as your sole defense in today’s world of sophisticated ransomware attacks is a recipe for disaster.
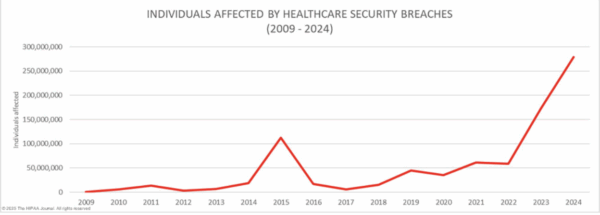

This article will break down why the “HIPAA-is-enough” mindset is a dangerous gamble and provide a clear, practical path to building real security, one that doesn’t require a massive budget.
The Great Disconnect: HIPAA’s Weaknesses in a Modern Threat Landscape
HIPAA’s Security Rule was revolutionary in 1996, but its greatest strength then is its biggest weakness now: it only requires “reasonable and appropriate” safeguards. This vague standard creates dangerous gaps that attackers exploit every day.
Think of it this way: HIPAA is a building code that says every house needs “a lock on the door.” But it doesn’t specify if that lock should be a simple doorknob latch or a reinforced deadbolt. It doesn’t mention alarm systems, security cameras, or what to do if someone breaks a window.
- Lack of Prescriptiveness: HIPAA doesn’t explicitly require modern security controls like Security Information and Event Management (SIEM), 24/7 log monitoring, or advanced threat detection. As a result, many organizations “check the box” with manual, inconsistent audit log reviews, leaving massive blind spots for attackers to exploit.
- No Maturity Model: Is your annual risk assessment a one-page checklist or a dynamic process that actually reduces risk? HIPAA makes no distinction. You can be compliant, yet incredibly vulnerable.
- Incident Response Gaps: The law gives you 60 days to report a breach after you discover it. But it offers no playbook for the chaos of that discovery. It doesn’t require a drilled response team, which is why so many organizations are caught flat-footed, missing deadlines and making a bad situation worse.
A prominent example is the CommonSpirit Health breach. In September 2022, hackers accessed the network of one of the nation’s largest health systems, exposing data from over 623,000 patients. Despite being HIPAA compliant on paper, CommonSpirit’s lack of advanced monitoring, immature risk processes, and a slow, untested incident response led to notification delays far beyond the 60-day HIPAA requirement, triggering lawsuits and regulatory scrutiny.
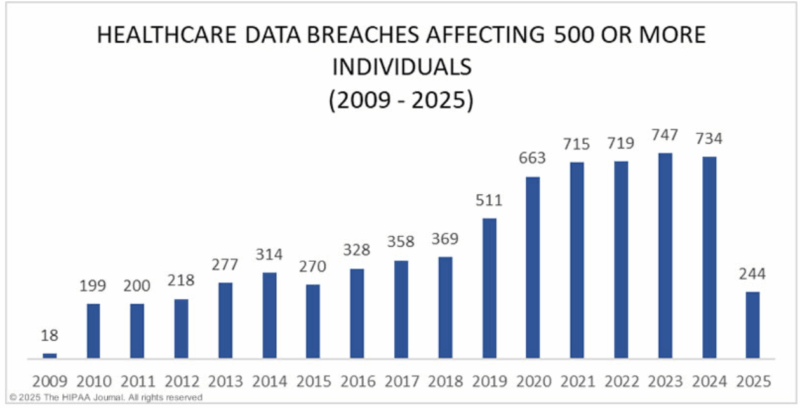

In January 2025, the federal government proposed an update the HIPAA in decades, including mandatory asset inventories, annual security audits, universal MFA, network segmentation, and encryption of all patient data. These changes are expected to be finalized in 2026, giving organizations only 180 days to comply. However, taking action now not only protects your patients and business, but also puts you ahead of the regulatory curve.
From Vague Rules to a Real Rulebook: Enter HITRUST
This is where a modern security framework like the Health Information Trust Alliance (HITRUST) Common Security Framework (CSF) is a game-changer.
HITRUST isn’t a replacement for HIPAA. It’s the detailed blueprint that shows you exactly how to build the secure house that HIPAA only vaguely describes. It translates vague requirements into a clear, actionable, and certifiable set of controls.
The Real ROI: Security is Cheaper Than a Breach
Many small practices fear the cost of robust security. But the cost of a breach is infinitely higher. The average cost of a healthcare data breach in 2024 for the U.S. was $9.7 million. Can your organization afford that?
Investing in a framework like HITRUST has a clear return:
- Prevent Catastrophic Costs: The investment is a fraction of the cost of a single major breach.
- Lower Your Cyber Insurance Bill: Insurers are demanding better security. Having a HITRUST certification proves you are a lower risk and can lead to significantly better premiums.
- Build Trust and Win Business: Certification is the new gold standard. It proves to patients, partners, and larger health systems that you take security seriously.
Your Action Plan: Real Security Doesn’t Require a Huge Budget
Adopting a framework like HITRUST is a journey, not a flip of a switch. You can start today with low-cost, high-impact steps that make you safer immediately.
Phase 1: Foundational Controls & Gap Analysis (Months 1-3)
Forget the massive budget for now. Focus on the basics that stop the most common attacks.
Your first goal is to control your environment and fix the most common entry points for attackers.
- Create an Asset Inventory: You can’t protect what you don’t know you have. Many breaches begin on forgotten servers or unmonitored devices. Action: Start a comprehensive inventory of all devices, software, and systems connected to your network. Use automated tools if possible, but even a detailed, consistently updated spreadsheet is a powerful start.
- Deploy Phishing-Resistant MFA: Don’t just “enable MFA.” For systems containing patient data (like your EMR and email, etc.), you need the strongest protection. Action: Mandate the use of phishing-resistant methods like FIDO2 security keys (e.g., YubiKey) or device-bound passkeys. This is the single most effective technical control to block account takeovers. Cost: Keys are a minimal investment per employee for a massive security upgrade.
- Secure Your Medical Devices: Connected medical devices are a massive and often overlooked risk. Action: Identify all connected medical devices (IoMT), from infusion pumps to imaging systems. Work to segment them from your main business network to contain any potential breach.
- Check Your Backups: Your backups are your last line of defense against ransomware. Action: Ask your IT provider: “Are our backups fully isolated and immutable?” If an attacker can encrypt your backups, they are worthless.
Phase 2: Build Your Foundation (Months 3-5)
- Develop a Simple Incident Response Plan: What do you do the moment you suspect a breach? Who do you call? Write it down. It doesn’t need to be 100 pages. A one-page checklist is better than nothing.
- Scrutinize Your Vendors: Your security is only as strong as your weakest partner. Ask your critical vendors (like your IT provider or billing company) for proof of their security, like a SOC 2 report or HITRUST certification.
- Start a Self-Assessment: Use the free HITRUST framework to see where your gaps are. This will create your roadmap for the future.
Phase 3: Mature and Certify (Months 5+)
Once you have the foundation in place, you can pursue a formal certification, like a foundational HITRUST i1 assessment. This provides a formal “seal of approval” that validates your security posture.
A Final Word: Don’t Wait to Become a Statistic
I’ve seen what happens when compliance is mistaken for security. I’ve read the notifications from organizations that thought they were safe because they were “compliant.” Don’t let your organization be the next one.
The question is no longer “Are we HIPAA compliant?” but “Are we secure?”
You can start answering “yes” to that question today.
Ready to take the first step? Here’s your immediate action plan:
- Research FIDO2 security keys for your leadership and staff with high-level access.
- Forward this article to your IT provider and ask them about implementing phishing-resistant MFA and checking your backups.
- Decide on a date for your first employee security awareness training.
Building real security is a journey, but it begins with a single, decisive step. Take it now. Because for us, like our Founder at Cyber News Live, even one victim is one too many.
By Joy Chopda, M.S. Cyber Security & Information Assurance, intern at Cyber News Live.
