

Identifying and Avoiding Phishing Scams in 2025
If you’re here, chances are you’ve either just come across the term “phishing” or recently fallen prey to this common cyberattack.
Phishing scams have become increasingly common—research by Statista shows that, since 2019, they’ve been the most frequently reported kind of cybercrime. What’s more, in 2023 alone, people reported almost nine million phishing scams globally.
Identifying and avoiding phishing scams can be tricky, but it’s not impossible. In this article, we’ll explain what phishing attacks are, how to spot them, and ways to avoid falling for one. Plus, we’ll discuss what to do if/when you’ve been phished.
What is Phishing and How Does It Work?
Phishing—pronounced ‘fishing’—is a cyber-attack where scammers trick people into revealing personal information (e.g. credit card numbers, Social Security numbers, and passwords) and confidential business data. In these scams, cybercriminals pose as legitimate individuals or organizations, urging you to take specific actions like:
- Clicking on attachments and website links infected with malware
- Filling out fraudulent data entry forms
Once you give up sensitive data to these scammers, they can use it to steal your money or identity and take control of your online accounts.
Phishing scams typically target people through emails, text messages, and phone calls. For example, you may get an email that appears to come from a reputable email service provider like Outlook.
This email may “inform” you of a recent system upgrade and ask you to immediately reactivate your account by clicking on a link.
This link may lead to a phony or “spoofed” website that resembles the email service provider’s website. Once you click the link, the website prompts you to enter your credentials, such as your username and password.
After submitting these details, the link redirects you to the organization’s real website so you don’t immediately suspect anything.
The main types of phishing scams include:
- Email phishing involves using emails that appear legitimate; these emails usually ask you to open an attachment, reply with personal information, or click on a link.
- Pop-up phishing involves using fake pop-ups for users when they’re surfing the internet. These attacks mostly trick people into installing malware by highlighting a problem with their computer’s security or other issues.
- Spear phishing targets a specific individual within an organization to lure them into submitting private information. Before the attack, the phisher may have already gathered information about this person—including their name, contact details, and their position in the company.
- Voice phishing (aka vishing) happens when a scammer calls you and pretends to be a trusted person or organization so they can steal your info.
- Text phishing (aka smishing) uses text messages that contain clickable links or return phone numbers.
- Angler phishing is a form of phishing attack where cybercriminals create fake social media accounts that look like popular brands. They use these accounts to respond to social posts and subsequently trick people into providing their information.
- Pharming attacks involve using malicious code to direct victims from a safe website to a fake or spoofed one.
- Clone phishing occurs when scammers duplicate a real message that was previously sent. The difference is that they replace legitimate attachments and links with malicious ones.
- Evil twin phishing happens when a scammer creates a fake Wi-Fi network that mimics a legitimate one. Once someone connects to the network, the attacker can intercept all the information transmitted by the user.
How Can You Identify a Phishing Scam?
Today, phishing attacks have become more sophisticated and elaborate, so they can be harder to detect.
However, there are still some tell-tale signs that can help you spot a phishing attempt:
- Irrelevant and out-of-the-blue messaging: One way to identify a phishing scam is by carefully scanning the content of the message. If it’s random and unrelated to your recent activities or usual interests, there’s a high chance that it’s a phishing attempt. For example, you may receive an email claiming to be from your bank. This email may ask you to verify information about a transaction you never made.
- Contains suspicious links and attachments: Phishing emails usually include unsolicited attachments with unusual file names and end with .zip or .exe. Plus, you may find suspicious URLs that don’t match the sender’s claimed identity. You can spot fake links by checking their structure—secure URLs begin with “https://” not “http://.”
- Filled with poor grammar and spelling mistakes: If you see an email or SMS with bad grammar and multiple typos, it’s likely a phishing scam. Professional and legitimate companies hardly send out poorly written or edited emails to their subscribers.
- Generic greetings: Another way to spot a phishing message is by checking the greeting. Does it begin with a generic “Dear Customer”, “Dear Sir/Madam,” or “Dear User?” If so, it may be a phishing attack as real companies normally address their customers by their names.
- Misspelled and illegitimate email domains: Check the last part of the sender’s email address. There’s a very slim chance (if any) that a reputable company will send you emails from a public domain like “com.” Phishing emails are usually sent by addresses that don’t match the company they claim to be from. Plus, look out for misspellings of a company’s legal domain name. Phishers often add random characters or slightly misspell addresses to make them seem official. For example, they may use “support@paypa1.com” in place of the real address, which is “support@paypal.com.”
- Urges you to act fast and invokes fear: One surefire way to recognize phishing emails is by examining their language. Most of them attempt to create a sense of urgency or scare you into taking action “immediately.” For example, they may urge you to “act fast/now” to claim a reward or tell you to “verify your account” to avoid suspension.
Unprofessional or inconsistent design: Watch out for emails that lack professional formatting or low-quality graphics.
11 Ways to Protect Yourself from Phishing Attacks
In this section, you’ll discover 11 proven steps and measures to take to avoid being a victim of phishing scams.
1. Be cautious with emails and messages
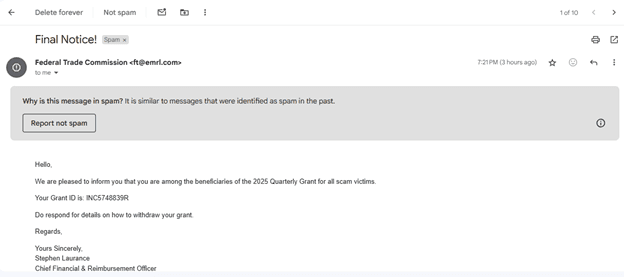

First, you need to be careful with any email or message that looks unexpected or fishy. If it’s characterized by any of the factors we mentioned in the previous section, don’t respond to it.
For example, check out the image above. This is clearly a phishing attempt due to a variety of factors:
- The sender’s email address doesn’t resemble an official Federal Trade Commission (FTC) domain, which should typically end in “.gov.”
- The messaging isn’t personalized.
- There is nothing like a “2025 Quarterly Grant for all scam victims.”
- No government agency offers unsolicited grants without prior application.
- Tries to compel the reader to act quickly by using “Final Notice!” in the subject line.
To verify whether it’s really from the company stated in the message, use the phone number or email address on their official website to contact them directly.
Also, if the suspicious email seems to come from someone you know, it’s more advisable to contact that person—preferably through a phone call.
2. Use multi-factor authentication
Another way to ensure your safety online is by enabling multi-factor authentication for any account you use that supports it.
This means that you’ll need to provide two or more credentials before logging into your account. For example, you might need to first submit your password and then answer a security question.
3. Don’t click suspicious links or attachments
Avoid clicking on links and attachments from unverified sources or unknown senders so your device doesn’t get infected with malware.
If you’re not sure about any link, you can hover over it without clicking (on a laptop) or press the link (on a mobile device). If the address that shows doesn’t match the link contained in the message, it’s most definitely a phishing link.
Some scammers also use embedded links or short URLs like bit[.]lys in their emails, so you should be wary of these as well.
If you want to confirm the email’s legitimacy, visit the company’s official site via a web search.
Also, remember not to click links on websites that aren’t trusted.
4. Install antivirus and anti-malware software
Make sure you install antivirus and anti-malware software on all your devices. These programs can detect and block malicious files, suspicious links, and phishing attempts in near real-time.
5. Regularly update your software
It’s also important to keep your browsers, operating systems, apps, and security software up to date. Software updates and patches can fix security vulnerabilities that scammers often exploit.
Pro tip: Enable automatic updates wherever possible.
6. Use firewalls
A firewall is a network security device that monitors, filters, and controls traffic to and from your network. Simply put, they protect your network from unauthorized access and malicious traffic that could lead to phishing attempts.
Firewalls can either be hardware or software. Setting up both of them for your device can add extra layers of defense and reduce your chances of falling for a phishing scam.
7. Check for a website’s security
Before submitting personal or financial information to any website, you need to ensure that it’s secure.
Check the site’s URL to confirm that it begins with https instead of http as the former establishes a secure connection using encryption.
Also, look for a padlock icon next to the address bar—this confirms that the website has a valid SSL certificate.
8. Watch out for pop-ups
In the previous section, we mentioned how scammers create fake pop-ups that appear to be from authentic organizations. These pop-ups may require you to log in or enter payment information.
To ensure safety while browsing, avoid clicking on pop-ups as they’re most likely always phishing attempts. You can block them using your browser’s settings or a trusted pop-up blocker.
If a pop-up appears despite these measures, don’t close it by clicking the “cancel” button, as this can redirect you to phishing sites. It’s better to:
- close the whole tab
- restart your browser
- press Ctrl+Alt+Delete to open your Task Manager, find the browser, and select “End Task”
9. Don’t click “Unsubscribe”
If you receive emails from unknown sources or phishers, don’t click the “Unsubscribe” button. If you click on it, it may prove to scammers that your email address is active and lead to increased phishing attempts. What’s more, doing so may set off the installation of malware on your device.
The best thing to do to block emails like these is to mark them as spam.
10. Be careful when using public Wi-Fi
Avoid accessing sensitive information while you’re using public Wi-Fi. Plus, use a Virtual Private Network (VPN) to encrypt your web traffic and ensure that cybercriminals don’t intercept your data.
11. Stay on the pulse about phishing methods
One effective way to outsmart phishers is by learning about phishing techniques and staying informed about new scams—just like you’re doing by reading this article.
What to Do If You’ve Been Phished
Suspect you’ve accidentally fallen for a phishing scam? It’s normal to panic but you need to keep a clear head and act quickly to minimize the damage.
Here are some effective steps to take:
1. Change passwords
As fast as possible, change the passwords of each (potentially) affected or compromised account. Ensure that these new passwords are strong and unique.
2. Disconnect from the internet
If malware infects your device, disconnect it from the internet immediately.
This way, you can prevent other devices connected to the same network from malware infection.
3. Alert your financial institution
If you reveal your financial details in a phishing attack, contact your bank or credit card company right away to report the incident. This way, they can monitor your account for fraudulent activity and freeze it (if necessary.)
4. Keep a close eye on your accounts
Monitor your email, bank accounts, or other online accounts for any unusual activity.
Once you detect anything suspicious—such as changes to account settings, fraudulent transactions, or unauthorized logins—report it immediately.
5. Report the incident
Report any phishing email, message, or website to the relevant authorities, such as the email provider, the company the phisher was posing as, your country’s cybercrime agency, or the Anti-Phishing Working Group.
By doing this, you can raise awareness, help others, and assist these organizations in fighting scammers.
6. Notify your contacts
Scammers may use your compromised accounts to target your family, friends, or coworkers next.
To ensure they don’t fall victim to phishing attempts, inform them of the attack as soon as possible.
7. Scan your device for malware
Run a full antivirus/anti-malware scan on your device. This will detect and remove any malicious software installed after you click on a phishing link or attachment.
Wrapping Up
Phishing scams are continuously increasing and evolving, but you don’t have to live in fear of them. By staying alert and following the strategies outlined in this article, you can protect your data and stay safe online.
This article was brought to you by Blessing Halim, a skilled content writer and editor. For the past four years, she’s crafted informative, engaging, and SEO-friendly articles for businesses across various industries.
Eager for more cybersecurity tips and resources? Stay tuned to Cyber News Live!
If you’d like to be a freelance journalist, writer, or weekend warrior with Cyber News Live, please email us at contact@cybernewslive.com. Thank you!
