

The Silent Epidemic: Millions Caught in the Crossfire of Cyber Attacks
Have you found yourself caught in the silent epidemic of cyber attacks? Ever wondered what happens when your data ends up in the wrong hands? Maybe you have received a notification that your passwords or privacy has been compromised and felt unsure about what to do next. Over the past six months, we’ve been researching, analysing, and reporting on these breaches and exploring the steps that can be taken to stop this alarming rise in cyber crime. Now, we’re ready to share our findings with you. Here’s what we discovered.
Key Findings:
Our reports find that between January 01 to June 30, 2024:
- 146 million victims.
- 500 companies.
- 800,000 victims per day.
Total number of victims, companies per month, and victims per day
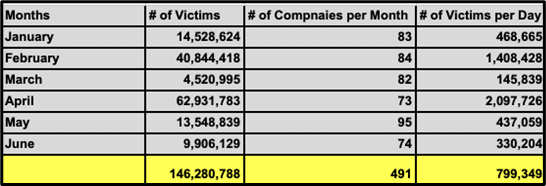

*This report is based on official government data. The estimated victims include employees, contractors, and clients, though many victims remain undisclosed or unknown.
As we look back from January 1 to June 30, 2024, we see that just under 500 companies have reported data breaches affecting themselves and their clients/consumers. But what are these companies doing to protect your information and privacy? Are they doing enough? Why do some companies wait weeks, months, or even years before disclosing a breach?
These variations are influenced by factors such as government regulations, including those from the Securities Exchange Commission (SEC), Federal Communications Commission (FCC), New York State Department of Financial Services (NYDFS), and General Data Protection Regulation (GDPR), among others.
As we’ve highlighted, most companies’ breach notification disclosure windows vary from days to weeks, months, or even years. Should this be more strictly regulated?
Total number of victims per month
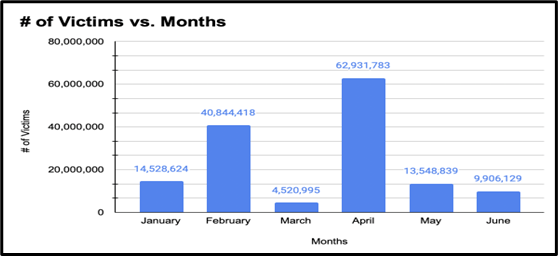

With so much time passing since the initial breach, you can’t be certain what private information has been compromised or exposed to phishing scams, malware, and other cyber attacks. That’s why continuously implementing multiple layers of protection is crucial for ensuring that only authorised users access sensitive information. Regular data backups safeguard against data loss, allowing you to recover critical information in case of accidental deletion, hardware failure, or cyber attacks.
Employing security software and tools, such as firewalls, antivirus programs, and encryption, detects and prevents unauthorized access to your systems. Additionally, fostering awareness and providing training to users is crucial, as informed employees can recognize and respond to security threats, reducing the risk of human error that could compromise your data. Combining these strategies builds a robust defense against a wide range of data security risks.
A proactive and layered approach to data protection is more important than ever in today’s rapidly changing digital environment, where cyber threats become increasingly advanced. By continuously reinforcing your defenses with robust authentication methods, regular backups, advanced security tools, and comprehensive employee training, you can significantly reduce the risk of data breaches and unauthorized access. Remember, data security is not a one-time effort but an ongoing process that requires vigilance and adaptation to new challenges.
Cyber Ecosystem
At Cyber News Live, We proactively advocate for our audience’s privacy and security by calling out companies with unethical approaches to handling customer data and information. We do this not to criticize these companies but to highlight the broader cyber ecosystem. Our mission is to bridge the gap in cyber news by integrating it into everyone’s news feed in a way that tailors to our audience members. We aim to create awareness and set a standard for delivering easily digestible and actionable information, helping our members adapt to the ever-changing digital environment. We simplify breach information so you can easily understand and act upon it. If you found yourself caught in the silent epidemic of cyber attacks, here is how you can protect yourself:
Change your passwords
First and foremost, update the password for the account affected by the data incident. Often, there is so much data stolen that customers have the opportunity to prevent unauthorised use of their accounts. Yes, we know you’ve been advised repeatedly not to use the same password for multiple accounts. Cyber criminals can easily access other accounts with the same or similar passwords. Reset passwords for any linked accounts. Use a passphrase with special characters and numbers for added security. Ideally, create a passphrase with at least 16 characters, though 8 characters is acceptable.
Use two-factor authentication
Even if someone else knows your password, two-factor authentication (2FA) will prevent them from accessing your account without authorisation. It is strongly advised that you enable 2FA if it is available on the platform or website in question.
2FA works in two primary ways. One method uses an authentication app on your phone. This is preferred over receiving codes via SMS. Authentication apps are safer because phone numbers can be stolen and SMS messages can be intercepted. To use the app, open it, view the code, and enter it to sign in and authenticate.
Monitor your accounts
To identify the precise type of data that may have been stolen, it is crucial to determine which accounts on which platforms were compromised. Users can monitor whether their account credentials have been exposed to a data breach using various services.
Identify which specific account was compromised. Check for any cascading effects that might affect your other accounts. Contact the company involved in the data breach for additional information and recommendations on how to protect yourself.
Check your credit reports
Be prepared for the worst: a data breach can lead to identity theft and fraud. Discovering a compromised account is distressing. Restoring access is challenging but minor compared to issues if someone uses your information for fraud. If a company storing financial data suffers a breach, review your credit report. Consider freezing your Social Security Number (SSN). Explore all options available to you through credit bureaus.
If you have been a victim of identity theft, immediately alert your bank and credit institutions. You should freeze your credit, apply for a new credit card number, and even close your accounts. Victims of identity theft are encouraged to report the offense at identitytheft.gov.
Additionally, most users will find that they need to reset their passwords and enable two-factor authentication. However, if you are one of the more vulnerable victims of a data breach, and your data has been used for financial theft, it’s crucial to act quickly to protect your funds.
Many companies cover credit monitoring costs for 1 month, 1 year, or up to 2 years, depending on the breach’s severity. However, who pays for monitoring afterward—whether it’s insurance, the company, or the individual—remains unclear and undefined. Therefore, it’s crucial to take preventative measures like freezing your SSN, authorizing two-factor authentication, changing passwords regularly, and monitoring your accounts. If you’re unsure of the next steps, contact us for assistance.
This article, “The Silent Epidemic: Millions Caught in the Crossfire of Cyber Attacks” was authored by Jennifer Riquelme, a 2024 Cyber News Live Summer Intern.
If you’d like to be a freelance journalist with Cyber News Live, please email us at contact@cybernewslive.com.
